Whilst we await the release of Shared Channels to Public Preview by end March 2022, there are a couple of things Administrators can be doing to prepare for, or indeed block, Shared Channels in Microsoft Teams.
DISCLAIMER: I am writing this article based on the information from the public announcements of Shared Channels (aka Teams Connect) and the settings discovered in my production tenant at the time of writing. It is possible that these features will change before and during public preview.
EDIT: For those who read this post on its original format, it has been updated. Cross Tenant access settings were not correct. B2B Direct Connect settings are the ones which control shared channels
Firstly, what are Shared Channels? Shared Channels were originally (and officially still are) called Teams Connect. They give you the ability to invite people to a channel in Teams, rather than the whole Team. They differ from Private Channels in that you do not need to be a member of the Team to be a member of a Shared Channel. Another big advantage of Shared Channels is that you will not need to switch tenants to see channels you are a member of regardless what organisation hosts the channel. Finally you will be able to invite whole Teams to a Shared Channel rather then just individuals and this includes Teams in other organisations.
The table below summarises the different features between the 3 types of channels in Teams
| Standard Channel | Private Channel | Shared Channel |
| All Team Members are members of the channel | Only invited Team Members are members of the channel | Anyone can be invited to the channel without needing to be a member of the Team |
| Supports External members | Supports External Members | Supports External Members |
| Full range of Tabs | Limited range of Tabs (Notable exclusions are Planner & Channel Calendar) | (TBC, expected to mirror private channels) Limited range of Tabs (Notable exclusions are Planner & Channel Calendar) |
| Can invite Internal Teams, Internal Users, Guest Users with MSA & AAD | Can invite Internal Teams, Internal Users, Guest Users with MSA & AAD | Expected to support only B2B AAD users & Teams, both Internal & Guests, as relies on cross tenant access settings which do not include options other than for AAD. |
Definitions
- AAD = Azure Active Directory (Enterprise/Business/Education/Government)
- B2B = Business to Business (refers to a relationship between two AAD tenants)
- MSA = Microsoft Account (Personal/Family)
NOTES: I’ve kept these definitions purposefully simplistic. There are lots of nuances and details when working with identity (accounts) across organisations.
Whilst we expect the documentation on Shared Channels to be released with the public preview, there is already some useful information available on cross tenant access setting for Azure AD on Microsoft Docs. This feature will underpin collaboration between organisations, which Shared Channels will rely on.
In my production tenant, which is set to Targeted Release for Everyone, I do have these Cross Tenant Access Settings in the Azure AD Portal. In addition Shared Channel settings have appeared in the Teams Policies when working via PowerShell, though not in the Teams Admin Center.
If you wish to enable your users to use Shared Channels during the Public Preview, you will need to:
- Configure Cross Tenant Sharing Settings
- Allow access to the Public Preview in Teams via an Update Policy for Teams
- Allow use of Shared Channels via the Teams Policy
If you wish to BLOCK Shared Channels for now, then you should disable B2B direct connect in Cross Tenant Sharing. This is the DEFAULT state tenants. You do not need to change the Teams policies for public preview and channel settings, however you may wish to use the Teams policies in place of disabling cross tenant sharing if you wish to allow selected users to test the features.
Disable Shared Channels
To Block all Shared Channel Features within your tenant and for users in your tenant, you need to configure default Cross Tenant Sharing to block all inbound and outbound collaboration. To do this:
- Navigate to the Azure AD Portal (https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview)
- Select External Identities > Cross-tenant access settings (Preview)
- Choose Default settings

- Select Edit inbound defaults then select Block Access for B2B direct connect for All External users and groups
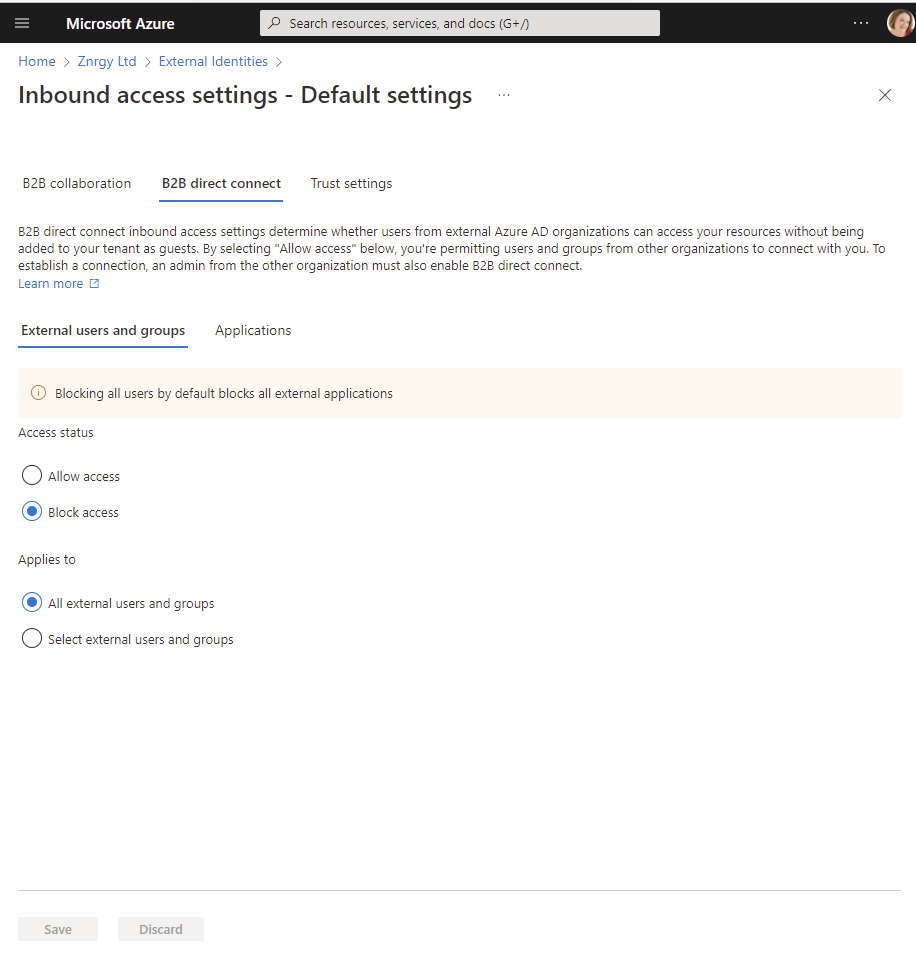
- Select Applications and choose Block Access

- Save your changes
- Under Trust settings ensure all boxes are unticked and Save changes
- Choose Edit outbound defaults then B2B direct connect
- Block access for both Users & groups and External Applications
- Save your changes
- The Default settings should now look like this:

For the avoidance of confusion amongst users it is probably advisable to block all shared Channel activity in Teams too. Currently you need to modify policies using Powershell. This example would create a new Teams policy to block all Shared Channels called “No Shared Channels”:
New-CsTeamsChannelsPolicy -Identity NoSharedChannels -AllowSharedChannelCreation $false -AllowChannelSharingToExternalUser $false -AllowUserToParticipateInExternalSharedChannel $falseNOTE: In the Teams Admin Center the Shared Channel settings do not show in that policy for all.

To block all shared channel features in the Global Policy, you would use
Set-CsTeamsChannelsPolicy -Identity Global -AllowSharedChannelCreation $false -AllowChannelSharingToExternalUser $false -AllowUserToParticipateInExternalSharedChannel $falseTeams policies can be assigned to individual users or Groups using Teams Admin Center, as well as using Powershell. For details on the various methods of assigning Teams policies to users, please refer to this article on Microsoft Docs.
When the shared channels features show in the Teams Admin Center the features can be configured as follows to block shared channels.
Allowing Shared Channels
To Permit Shared Channels with Specific Organisations is a 3 step process:
- Step 1 – Configure Cross Tenant Sharing
- Step 2 – Teams Update Policy
- Step 3 – Teams Policy for Channel Settings
These instructions, assume you want to open communication with a specific organization, whilst it is possible to open communication with any organization, the recommended approach is to configure access per organization as shown here.
Step 1 – Configure Cross Tenant Sharing for a Specific Domain
- Navigate to the Azure AD Portal (https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview)
- Select External Identities > Cross-tenant access settings (Preview)
- Choose Organizational settings
- Select + Add organization
- Search for the organization using domain name. Please remember that many organisations have multiple domain names registered. To avoid confusion, it is best to check with a Microsoft 365 administrator at the partner organisation for the domain. This will also allow you to verify tenant ID before opening up collaboration to ensure you are opening your doors to the correct organization!
- Select Add

- The new tenant will be added with both inbound and outbound settings inherited from default settings.

- To customise the inbound settings click Inherited from default link
- Under B2B collaboration for both External users and groups and Applications select Customize settings and choose Allow access on both for either All users or selected users/apps.
- Under B2B direct connect for both External users and groups and Applications select Customize settings and choose Allow access on both for either All users or selected users/apps. For Teams Shared Channels, if you choose selected applications you will need to add Office 365
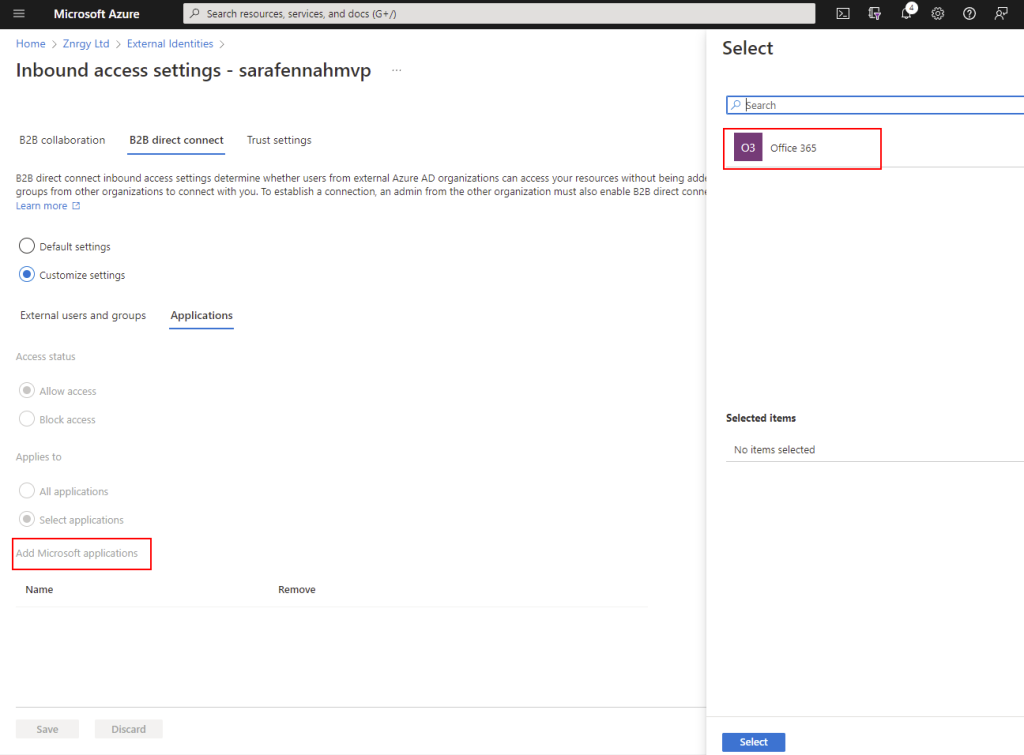
- Verify Trust settings. The exact configuration is not specified for Shared Channels. In terms or barrier to usage, I would recommend enabling Trust multi-factor authentication from Azure AD tenant as a minimum to reduce sign in and authorization friction for external users in shared channels.
Step 2 – Teams Update Policy
To use Shared Channels curing preview, users will need to be allowed to use Teams Public Preview. For details about enabling and using public preview see this article on Microsoft Docs.
Step 3 – Teams Policy for Channel Settings
For testing purposes it is recommended that you create a new Teams Policy which can be assigned to selected users for testing. The following script will create a policy called Creator which permits the use of Shared Channels.
New-CsTeamsChannelsPolicy -Identity Creator -AllowSharedChannelCreation $true -AllowChannelSharingToExternalUser $true -AllowUserToParticipateInExternalSharedChannel $trueIf you are using a test tenant, you may wish to set the default Global policy to allow Shared Channels using:
Set-CsTeamsChannelsPolicy -Identity Global -AllowSharedChannelCreation $true -AllowChannelSharingToExternalUser $true -AllowUserToParticipateInExternalSharedChannel $trueYou will then need to assign the policies to appropriate users. For details on the various methods of assigning Teams policies to users, please refer to this article on Microsoft Docs.
Once the settings appear in the Teams Admin Center, to permit shared channels the policy should be configured as follows:

Below is a screen shot of the script file I used preparing this article which you can download below.

Alternative link to file if download does not work


Thanks for this great article. However the download of the script is blocked.
LikeLike
Alternative link added for download
LikeLiked by 1 person